By Dan Goodin, Ars Technica » Risk Assessment – August 28, 2012 at 10:46AM
Last week’s feature explaining why passwords are under assault like never before touched a nerve with many Ars readers, and with good reason. After all, passwords are the keys that secure web-based bank accounts, sensitive e-mail services, and virtually every other facet of our online life. Lose control of the wrong password and it may only be a matter of time until the rest of our digital assets fall, too.
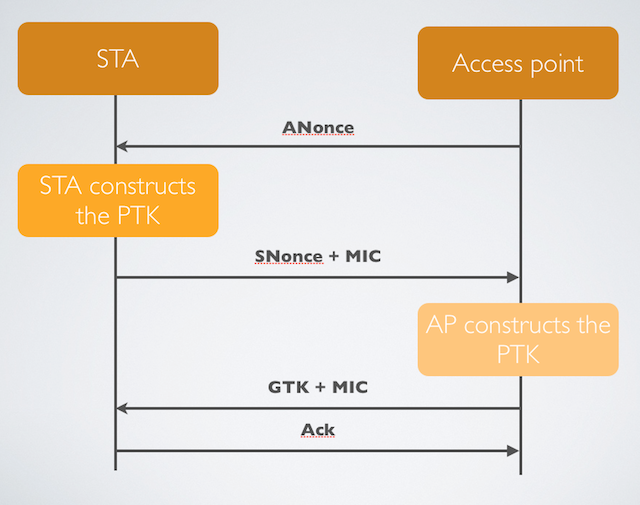
Take, for example, the hundreds of millions of WiFi networks in use all over the world. If they’re like the ones within range of my office, most of them are protected by the Wi-Fi Protected Access or Wi-Fi Protected Access 2 security protocols. In theory, these protections prevent hackers and other unauthorized people from accessing wireless networks or even viewing traffic sent over them, but only when end users choose strong passwords. I was curious how easy it would be to crack these passcodes using the advanced hardware menus and techniques that have become readily available over the past five years. What I found wasn’t encouraging.
First, the good news. WPA and WPA2 use an extremely robust password-storage regimen that significantly slows the speed of automated cracking programs. By using the PBKDF2 key derivation function along with 4,096 iterations of SHA1 cryptographic hashing algorithm, attacks that took minutes to run against the recent LinkedIn and eHarmony password dumps of June would require days or even weeks or months to complete against the WiFi encryption scheme.
Read 13 remaining paragraphs | Comments